Top Secret #2 : Top Mail released
What is Top Mail for ?
Top Mail is a mass-mailing tool with some special particularities :
- The attachments are individually marked to let you know who leaked the document !
- The mailing compain is saved encrypted into a cover file : JPG, PNG or PDF.
If you have to distribute an internal document into your business, stakeholders or investors, you would like to mark it in order to know who leaked the informtion.
Top Mail aims to do this in a very clean manner. No visual impact, no doubt.
Let's dive into !
Download the executable jar here and its libraries in the same folder.
Launch TopMail.jar and begin your emailing compain right now.
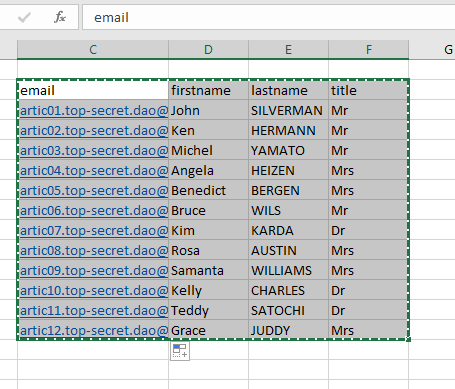
Only the "email" column is mandatory. All other columns are at your own request according to your needs.
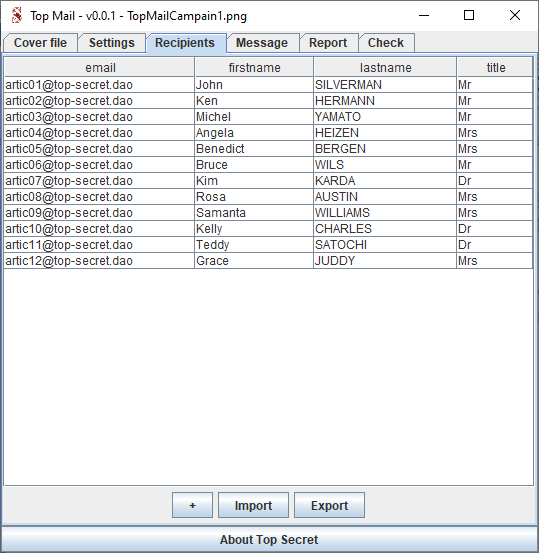
Go to the Recipients tab and click "Import" :
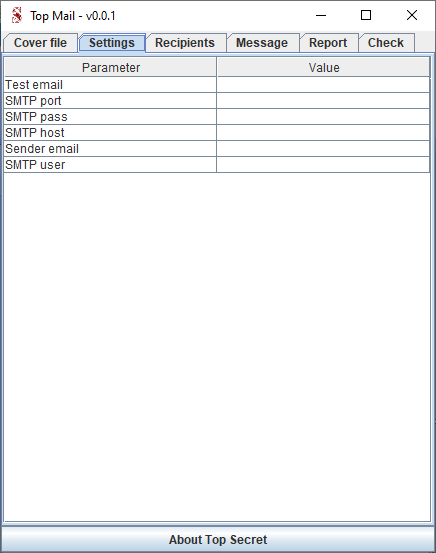
Important note : the "Test email" in the "Settings" tab must be an existing email address among the recipient list.
When clicking "Send Test", only this email will receive the test message.
When clicking "Send", all other emails will receive the message.
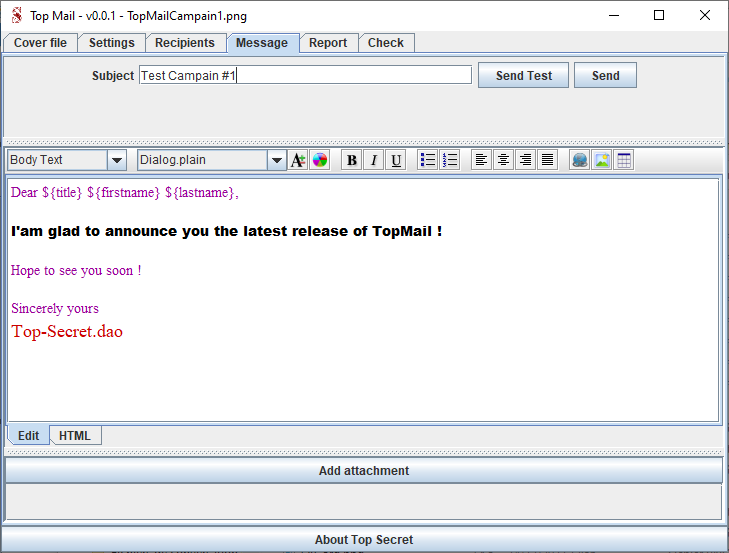
All the recipient columns are replaced by its corresponding value prior to sending each email. Enclose its name between ${...}
Now, click "Add attachment" and select one by one the files you want to join into the email.
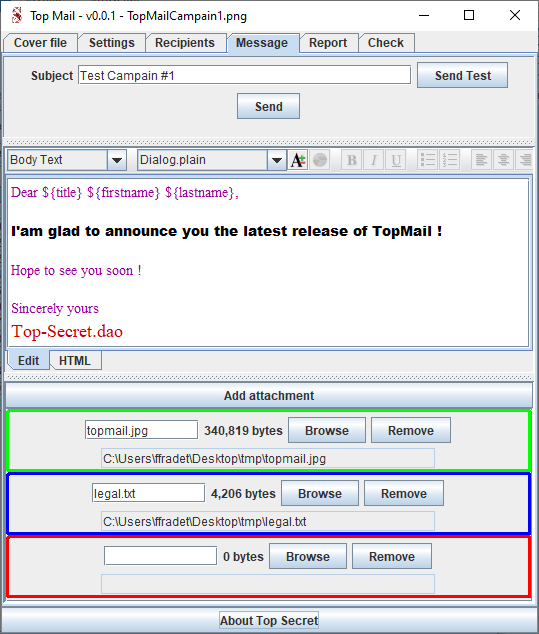
You can see a colored border.
Green means the File will be processed for marking
Blue means the File can not be marked but will be attached to the mail
Red means No file / File not found / Access denied and will be ignored
Let's now send a test mail !
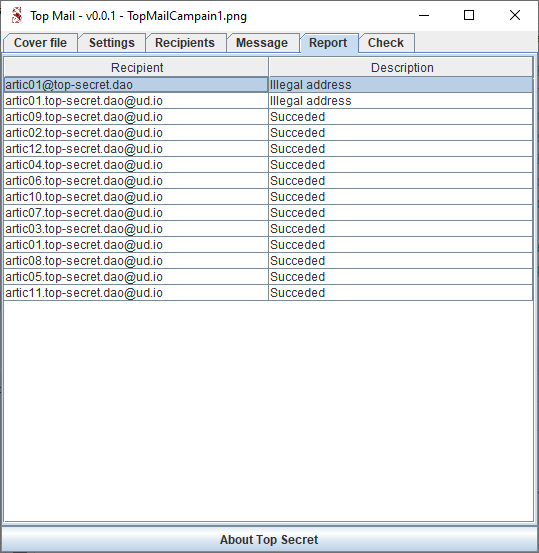
Then launch the mass-sender and see the Report section to go through troubleshoot.
Look at the "Check" section with the original green attachment :
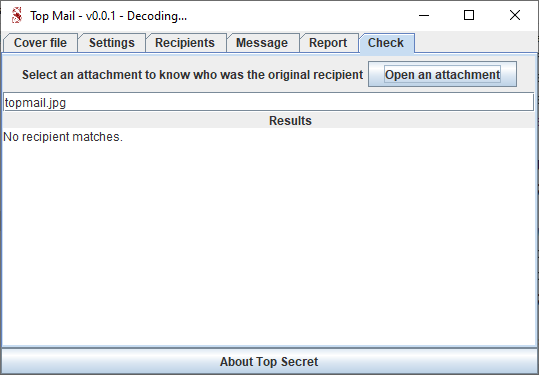
Now let's suppose you've found your confidential attachment somewhere on the web.
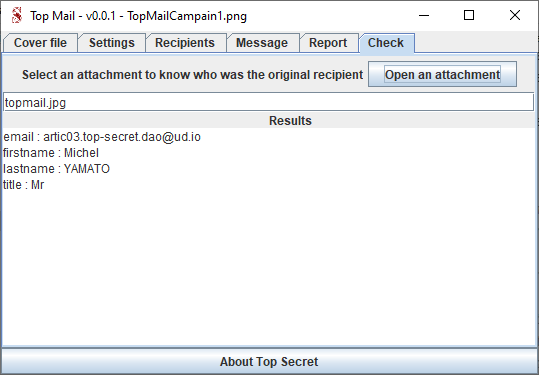
Note that the enclosed data into the attachment looks like a binary hash of the email salted with your own Master pass and Data pass using your Hash Algo. There is no possibility for any hacker to retrieve these personal data from the hash.
If you change your passwords and/or the hash algo, you would not be able to retrieve the recipient.
